Key management: learn from the successful
Improving the user experience of PGP is a key factor for wider adoption of email encryption. One of the major obstacles is the key exchange. If a manual key exchange is required before starting a secure communication with PGP, the barrier is often too high. This is shown by studies like "Why Johnny still can't encrypt".
The success of the Signal protocol, which is or will be used by almost all big players in the messenger market, reminds us that a deployment of end-to-end encryption is possible for billions of users.
But not with a manual key management, or as Matthew Green has put it in his post "What’s the matter with PGP?":
Manual key management is a mug's game. Transparent (or at least translucent) key management is the hallmark of every successful end-to-end secure encryption system. Now often this does involve some tradeoffs -- e.g., the need to trust a central authority to distribute keys -- but even this level of security would be lightyears better than the current situation with webmail.
In this post we want to present our approach to transparent key management and further user experience improvements.
The new Mailvelope user experience
Mailvelope v1.5.0 focuses on improving the user experience in several key areas.
Gmail integration
Google Mail and Google App users no longer need to enter recipient email addresses twice.
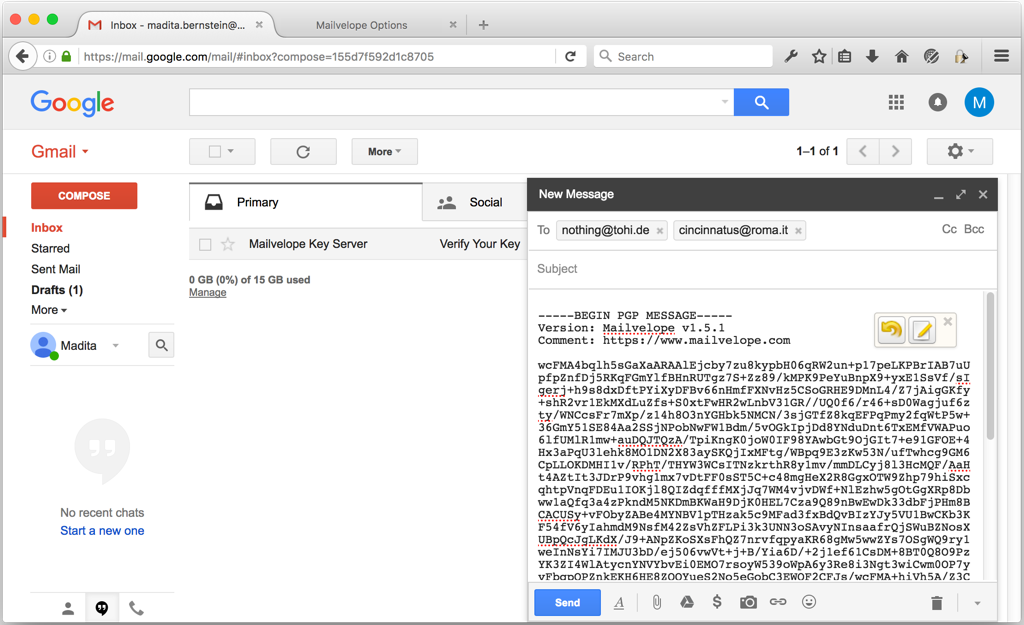
Mailvelope will read recipient addresses from the webmail UI when opening the editor to write encrypted messages. If the user adds or removes additional recipients, those will be transferred back to the webmail UI as well. Support for other webmail providers is planned.
Key management
If both the recipient and the sender are using the current release of Mailvelope, they will no longer need to exchange public keys manually.
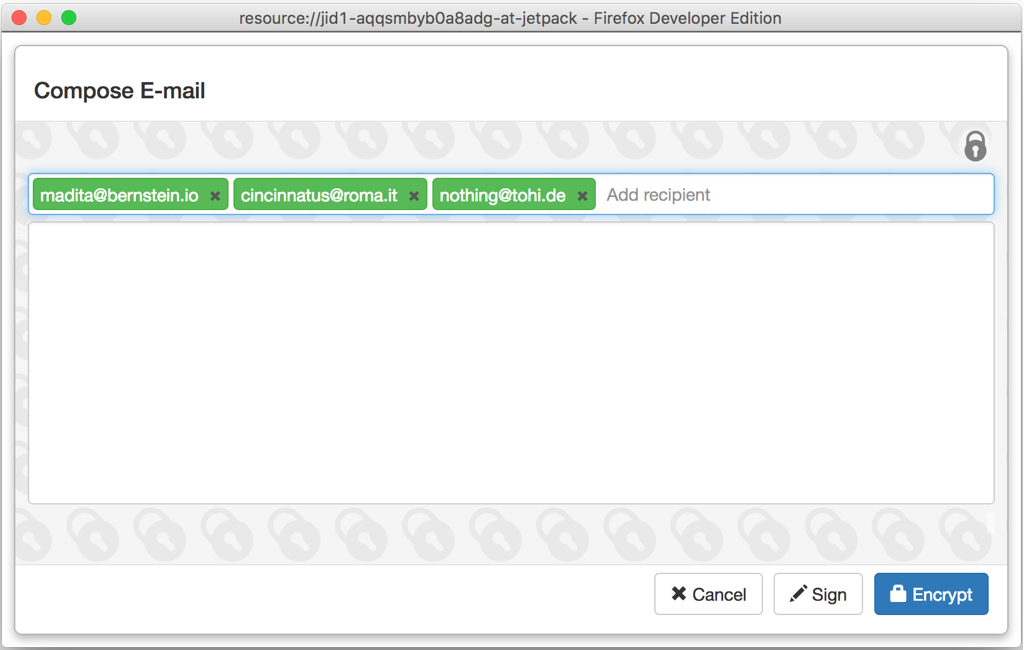
When writing a new message, public keys will be fetched automatically while typing in recipient email addresses. This will work for any Mailvelope user that has verified their email address using the current version.
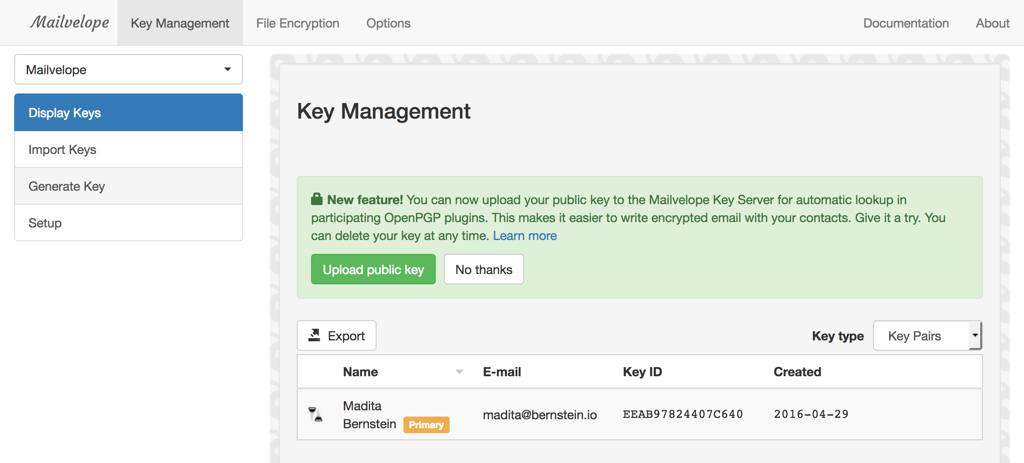
Privacy settings
While we would like to improve the usability for as many users as we can, we also understand that some users might not want auto-lookup and key upload to be enabled.
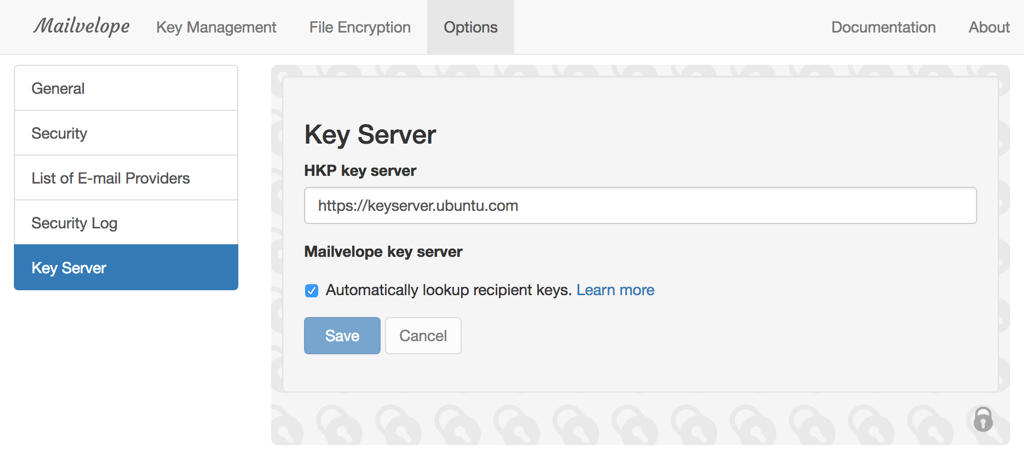
That’s why we’ve made it really easy to opt-out of auto-lookup and key upload. You can also delete your public key at any time, if you want to just give it a try and delete all your data from our server later. Our privacy policy is in plain english and you can review it here.
The Mailvelope key server
This new and improved user experience is fueled by a new piece of technology that we are excited to share today. We’ve built a simply key server that works similarly to the Signal backend. It verifies email addresses using an encrypted verification email. This not only verifies email address ownership but also provides cryptographic proof of private key ownership.
You can learn more about our key server at keys.mailvelope.com. The code is licensed under the AGPL v3.0 and is developed completely in the open on GitHub. If you’re a developer you can also learn more about the API in the documentation.
Cooperation with GPGTools and other OpenPGP clients
We want to make it as easy as possible to write encrypted email between users of different platforms and form factors. That’s why we’re excited to announce that we are working together with GPGTools for macOS to make it completely painless to write encrypted email between our users. GPGTools is in the process of integrating the Mailvelope Key Server and will also be providing an automatic key lookup user experience.
In addition, we are gathering feedback for the key server from the PGP community at the OpenPGP Summit in July.


